This post comprises a few selected parts of the TUHUND deployment and implementation methodology document. Though, implementation partners are given a full detailed guide along with formal training and maximum real time support, this post is to just give a brief idea of the process to the prospective partners. TUHUND deployment and implementation is very simple and quick. It assures high returns for the partners.
Lifecycle phases of TUHUND deployment and implementation methodology are as follows:
Normally only the first phase is accomplished in one go. Phases 2 to 5 go through several iterations.
Technical deployment steps are as follows:
That’s it. System is up and running with latest TUHUND software. Sign off from the Technical Deployment.http://www.tuhund.com/http://www.tuhund.com/
Two users with administrative access will be auto-created by the system and the credentials of one will be given along with the license. Other user access will be reserved for TUHUND support team access till deployment is complete. These two users will not be counted in TUHUND user licenses.
For data entry TUHUND recommends two diverse methodologies for the implementation.
The partner will have to select the correct methodology first, which can be any one or a combination of the two. The partner must then go through it thoroughly and explain the pros and cons of both the methodologies while negotiating the same with the customer. The selection must be made in real time considering the factors including but not limited to the following:
The partner is advised to put the methodology on paper and sign off with the customer so that customer expectations can be managed.
IMPORTANT: Please be advised, there can be a major problem with turnkey implementation due to the fact that all the departments in the customer's organization are highly inter-dependent on each other. If any department withholds the approval and / or their part of work, entire system comes to a halt.
For both types of implementation latest versions of sets of data templates, instructions and sample files together with pre-requisites can be downloaded through the implementer control panel and the populated files can also be uploaded in the same panel for population of data.
Now, let’s have a look at the Implementation Workflow, in both the methodologies recommended sequence of data entry is as follows:
You can start with the Data Entry as follow, however the data entry is quite a long procedure but kind of interesting when you start doing it. You can start by entering:
Once you enter the ERP user data Next step is to configure the user’s access rights, so you will start with creation of security groups with appropriate security rights in each group. Neither groups nor rights are mutually exclusive. Which mean, one user can be in any number of security groups and one access right can also be in any number of security groups. Thus any given user can have multiple roles and responsibilities. Assign security groups and branch level access to each user. To make it simple you can work both ways; that is for a particular user you can choose the branches or you can go to a branch and choose users who have access to that branch. Similarly you can select security groups for a user or go to a security group and select the users in that group.
After configuration of users next procedure is to
Then the next big thing is to set up accounting and finance module, so you will start with
After this, you can move on to Inventory module and start
Then you can set up this rest of the requirement in phases:
Then Sign off from the Data entry and the Configuration.
But in both the methodologies, adding of ERP users will be followed by the following process:
FYI: Implementation partners are encouraged to use the system of ECS for implementation project management. Various task / milestone templates are available for quick use.
IMPORTANT: things you should know before you choose which methodology is best for you,
Incremental Implementation: In this method data is populated on incremental basis and the customer starts working on the system with minimal data. This is lengthy method and takes more time of partner's resources. However, this is more dependable method and ultimately the customer gets to use the full power of the system sooner.
In two steps login ids of users can be created and users can log in. Thereafter, the sequence of data entry, training and signoff can be rearranged based on the priority and readiness after every stage.
The process can be roughly split into eight phases and can be completed within eight weeks.
Turnkey Implementation: In this method data is populated in one go and users can login to fully populated system and start working. The process can be repeated over several iterations after deleting data from the earlier iteration till the customer decides to keep the data and close the project as completed. The purpose of iterations is to provide a real time trial to the customer's resources with their own real time data.
Clearing of partial data is possible but should be discouraged as there can be inter-dependencies which, if not resolved, will cause errors at the production time. Leaving partial data on the server for repeated iteration does not save time but prolongs it. Templates are available for all data in excel format and uploading each template auto-enters data correctly in virtually no time.
The final phase implementation is the training. Training too is almost never done in one go even of it is for a single location. It is done over several sessions with planned breaks to allow the users to understand, practice and perfect themselves.
For training too, entire methodology, workflow and training material is provided by TUHUND. However, it is again recommended to use TUHUND training module for the same.
Having said all that, even after providing detailed implementation guide and training, TUHUND team from ECS Business Software Solutions will be their throughout the process to support you. You may also offload some or all of your data processing work to our back-office and we will be glad to assist.
Concluding word of caution : Time and effort will hardly depend on your technical capability or on the software. It will primarily depend upon the cooperation of your customer and the leadership of their executive management. Please quote accordingly.
Detailed lessons learned will be shared at the time of training.
Lifecycle phases of TUHUND deployment and implementation methodology are as follows:
- Technical deployment
- Data entry
- System configuration and tuning
- Training
- Signoff
Normally only the first phase is accomplished in one go. Phases 2 to 5 go through several iterations.
Technical deployment steps are as follows:
- Project formal start
- Procurement of TUHUND License for the buyer
- Hardware deployment
- Installation of RHEL 5.4 or higher (or Solaris)
- Network configuration
- Procurement and configuration of domains. Domain for ERP is mandatory while domains for customer sub-portal and recruitment sub-portal are optional
- Procurement and installation of secure server certificate (SSL)
- Install of Database Software
- Import blank TUHUND database
- Install JAVA and Apache Tomcat application server
- Install TUHUND License and scripts
- Run TUHUND auto update script
- Configure schedulers (crontab)
That’s it. System is up and running with latest TUHUND software. Sign off from the Technical Deployment.http://www.tuhund.com/http://www.tuhund.com/
Two users with administrative access will be auto-created by the system and the credentials of one will be given along with the license. Other user access will be reserved for TUHUND support team access till deployment is complete. These two users will not be counted in TUHUND user licenses.
For data entry TUHUND recommends two diverse methodologies for the implementation.
The partner will have to select the correct methodology first, which can be any one or a combination of the two. The partner must then go through it thoroughly and explain the pros and cons of both the methodologies while negotiating the same with the customer. The selection must be made in real time considering the factors including but not limited to the following:
- Nature of the organization and its geographic diversity.
- Current processes and maturity of the current processes.
- Current system or systems being used by the customer.
- Data export capability of the current systems to excel, CSV, xml formats.
- Involvement of the top management for leadership role.
- Number and authority level of the customer’s resources dedicated for the implementation project.
- Level of customization required that is mandatory before go live.
The partner is advised to put the methodology on paper and sign off with the customer so that customer expectations can be managed.
IMPORTANT: Please be advised, there can be a major problem with turnkey implementation due to the fact that all the departments in the customer's organization are highly inter-dependent on each other. If any department withholds the approval and / or their part of work, entire system comes to a halt.
For both types of implementation latest versions of sets of data templates, instructions and sample files together with pre-requisites can be downloaded through the implementer control panel and the populated files can also be uploaded in the same panel for population of data.
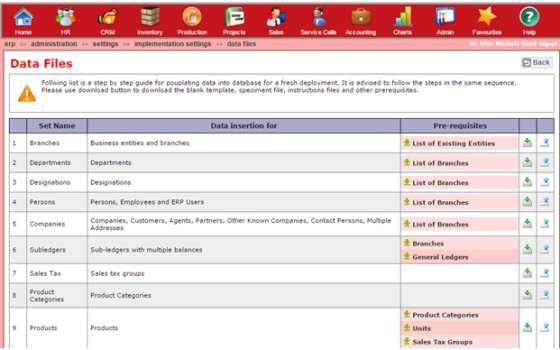 |
| TUHUND - Implementer Control Panel |
Now, let’s have a look at the Implementation Workflow, in both the methodologies recommended sequence of data entry is as follows:
You can start with the Data Entry as follow, however the data entry is quite a long procedure but kind of interesting when you start doing it. You can start by entering:
- Entity and branch data
- Departments and positions data
- Employee and ERP user data
Once you enter the ERP user data Next step is to configure the user’s access rights, so you will start with creation of security groups with appropriate security rights in each group. Neither groups nor rights are mutually exclusive. Which mean, one user can be in any number of security groups and one access right can also be in any number of security groups. Thus any given user can have multiple roles and responsibilities. Assign security groups and branch level access to each user. To make it simple you can work both ways; that is for a particular user you can choose the branches or you can go to a branch and choose users who have access to that branch. Similarly you can select security groups for a user or go to a security group and select the users in that group.
- Configure email servers and accounts
- Configure SMS API
- Configure user alerts and notifications
- Configure approval rules and workflows
- Notify users about their login ids and passwords
After configuration of users next procedure is to
- Create customer groups
- Create marketing zones
- Enter Customers, vendors and partners data
Then the next big thing is to set up accounting and finance module, so you will start with
- General ledgers tuning
- Entry of sub-ledgers and opening balances
- Configure smart accounts
- Create and configure transaction vouchers
- Create and configure accounting forms
- Configure currencies and exchange rates or exchange rate auto-update correction factors
- Create sales tax, service tax, GST, excise duty, secondary tax, add on tax (like nation building tax, suspended vat and zakat, etc) groups, whichever required.
- After accounting, Next step is to:
- Create product categories
- Configure sales units
- Products data entry
- Create service types
- Configure service units
- Services data entry
- Once all the product and services data is entered you can start with
- Creating quotation types and rules
- Create proforma invoice types and rules
- Create commercial invoice types and rules
- Create and configure price maps, price lists and rules
- Create lead referrers and categories
- Enter existing business leads
- Create event types and required fields
- Enter customer and lead events
- Enter open customer and lead reminders
After this, you can move on to Inventory module and start
- Creating stores
- Enter inventory
- Configure purchase order types
- Enter purchase orders
- Enter invoices
Then you can set up this rest of the requirement in phases:
- Configure project types
- Enter projects, tasks and resources
- Enter other tasks
- Create enquiry types
- Enter open enquiries
- Create service request categories
- Configure service rules
- Configure GRN types
- Configure Delivery note types
- Create and configure claim types
- Create and configure cost centers
- Configure financial statements
- Configure finance dashboard
- Re-configure all custom labels
- Re-configure all PDF templates
- Create new BI charts (if required)
- Test all backup scripts
Then Sign off from the Data entry and the Configuration.
But in both the methodologies, adding of ERP users will be followed by the following process:
- Create User Security Groups based on the roles as employees
- Assign security roles to users as per their job roles
- Print out roles map and discuss with the customer
- Re-configure and fine-tune security access.
FYI: Implementation partners are encouraged to use the system of ECS for implementation project management. Various task / milestone templates are available for quick use.
IMPORTANT: things you should know before you choose which methodology is best for you,
Incremental Implementation: In this method data is populated on incremental basis and the customer starts working on the system with minimal data. This is lengthy method and takes more time of partner's resources. However, this is more dependable method and ultimately the customer gets to use the full power of the system sooner.
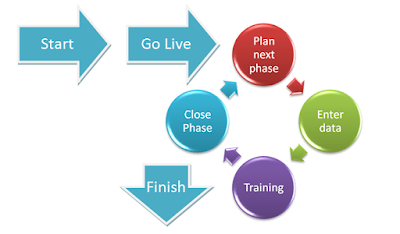 |
| TUHUND - Incremental Implementation work flow |
The process can be roughly split into eight phases and can be completed within eight weeks.
Turnkey Implementation: In this method data is populated in one go and users can login to fully populated system and start working. The process can be repeated over several iterations after deleting data from the earlier iteration till the customer decides to keep the data and close the project as completed. The purpose of iterations is to provide a real time trial to the customer's resources with their own real time data.
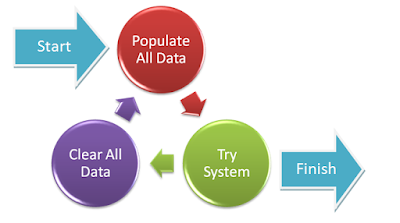 |
| TUHUND - Turnkey Implementation work flow |
Clearing of partial data is possible but should be discouraged as there can be inter-dependencies which, if not resolved, will cause errors at the production time. Leaving partial data on the server for repeated iteration does not save time but prolongs it. Templates are available for all data in excel format and uploading each template auto-enters data correctly in virtually no time.
The final phase implementation is the training. Training too is almost never done in one go even of it is for a single location. It is done over several sessions with planned breaks to allow the users to understand, practice and perfect themselves.
For training too, entire methodology, workflow and training material is provided by TUHUND. However, it is again recommended to use TUHUND training module for the same.
Having said all that, even after providing detailed implementation guide and training, TUHUND team from ECS Business Software Solutions will be their throughout the process to support you. You may also offload some or all of your data processing work to our back-office and we will be glad to assist.
Concluding word of caution : Time and effort will hardly depend on your technical capability or on the software. It will primarily depend upon the cooperation of your customer and the leadership of their executive management. Please quote accordingly.
Detailed lessons learned will be shared at the time of training.


Thanks to inform us about how to use sms API to send sms. it helps us to promote our services so get best Bulk SMS Service Provider in India to improve sale of your business product.
ReplyDelete